- Query about VoIP Service?
- +49 151 65127464
- sales@wdtel.com
How To Prevent SIP/VoIP Fraud Attacks

What is the Role of Transcoding in Telecom Business

The Importance of Virtual Session Border Controller

VoIP (Voice over Internet Protocol) might be the main tool for committing a fraud attack by fraudsters.
Voice over Internet Protocol (VoIP) services transmit telephone calls over high-speed internet connections instead of traditional fixed telephone lines. VoIP is the integration of resources and a way of saving money.
However –
-46% of fraudulent calls were made using VoIP phones within the first half of 2012.
These calls are usually not sent directly from the caller to the recipient’s computer, but through VoIP wholesalers or computers belonging to different levels of resellers. More successful attacks. As VoIP becomes more and more available, more successful attacks are occurring.
PSTN attacks and stem from traditional data networks are the most common threats to today’s VoIP deployment. In today’s article, you will know why these attacks are serious, what their types are, and ways to prevent them.
Types of VoIP Fraud Attacks
To prevent SIP/VoIP attacks, you must know their forms or how such attacks can appear. There are many types of SIP/VoIP attacks. More types are discovered from time to time.
Call Reselling, WANGIRI, IRSF (International Revenue Share Fraud), FAS (False Answer Supervision), Domestic Fraud, and PBX Hacking (probably the most popular) are some of the types of SIP/VoIP fraud attacks.
8 most common SIP/VoIP Fraud Attacks
Table of Contents
Now we will introduce you to the 8 most common types of SIP/VoIP attacks. Know about these attacks to be aware of them –
- PBX Hacking
Perhaps, this is the most obvious SIP/VoIP attack. This intrusion process mainly uses different types of IP PBX hacking software to gain access. Once access is granted, traffic will start to increase. Attackers also use this process to initiate calls to prime numbers.
- Denial of Services (DoS)

Distributed Denial of Service (DDoS) attacks are one of the most serious threats to VoIP phones. The main goal of DDoS attacks is to overload an unwanted system through excessive requests to force the existing system to shut down. DDoS attackers will try to compromise other nodes of the system by inserting malicious (such as Trojans) attacks and spoofing the original addresses and.
- Bypass Fraud
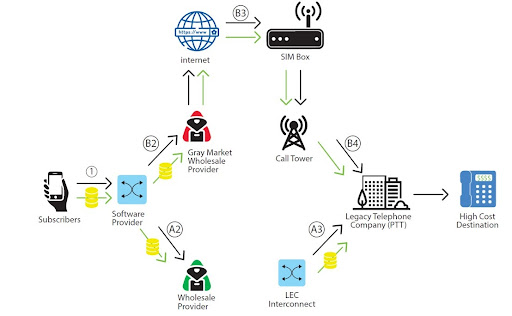
When unauthorized traffic tries to enter another operator’s network, then the process is called Bypass fraud. Here, the intention of the fraudsters is to bypass the usual international billing system by making international calls look like cheap domestic calls.
- CLI Spoofing and Robocalling
By spoofing a victim’s caller ID, a hacker can pretend to be a trustworthy person to an organization. Through this process, scammers can call victims to seek their personal information, bank account numbers, and one-time passwords for committing a cybercrime. Hackers or scammers use automated systems to generate traffic. A bot that can generate high traffic loads.
- Call Hijacking
Compared with traditional telephone networks, VoIP traffic is sent to the IP network in an unencrypted manner. And session sniffing becomes easier since there is no encryption used for the transmission of data traffic.
- Call Reselling
In this type of scamming, wholesalers add destinations to their price lists at far below standard prices. Other wholesalers get attracted to these offers. Since stopping traffic far below the standard price is not a viable method, wholesalers use it as a switch to invade the PBX. Wholesalers do not need to pay any fees and charge customers whose PBX is compromised for traffic.
- FAS (False Answer Supervision)
FAS is a type of fraud where one party in the traffic flow chain sends a false signal indicating that the call has been established, where no calls have actually been established. Billing when the call duration exceeds the correct value. The caller is billed according to – the connection time, completed calls, unconnected calls, setting up completed calls. The caller cannot connect to the called-party, but he needs to pay for the call time (related to answering calls).
These are key indicators of FAS detection –
- High answer seizure ratio
- Lower ACD
- Short phone calls
- Hangs up calls nearly 100% of the time
Aside from these, FAS detection Switch can be used to detect blended FAS which is quite common and done intentionally by the fraudulent suppliers. Also, there are systems to monitor FAS.
NetApp FAS Monitoring can be an excellent solution for FAS monitoring. It uses some of the modes like SSH Messages in NetApp Syslog, Cluster Mode SVMs (vFiler), Cluster Mode (CDOT), Non-Cluster Mode (7-Mode) to perfectly monitor FAS.
The VOS3000 FAS monitoring switch offers anti-spam traffic and exclusive anti-hacking support. It recalculates CDR, sets up IP addresses for DMZ, and applies other procedures to monitor FAS.
- SIP Registration Attack
Intrusion into SIP registration is a major VoIP security issue. In this process, the attacker separates users through a Denial of Service and tries to register with his IP address instead of the user’s IP address. So, a registration process occurs even before the SIP session is established, which may be hacked by an attacker.
How to minimize SIP/VoIP Fraud Attacks
Operators and service providers can protect their VoIP infrastructure, minimize these problems, and control access to VoIP services by using session border controllers. Strong protection can be provided by the SBC for IP communication infrastructure to prevent fraud and service theft. SBC is designed to support various types of SIP interoperability and provide guaranteed service to secure connections between VoIP networks.
FAQ
1) What are three advantages to using VoIP instead of traditional PSTN phone service?
Ans: There are many advantages of using VoIP phone service instead of the traditional PSTN. Take a look at the following benefits to get an idea –
- Advanced features for small to medium organizations
- Higher scalability
- Low costs
- Complete mobility
- Extended accessibility
- More convenient to softphones
2) Is SIP VoIP encrypted?
Ans: No, the problem is – we can’t encrypt the SIP information. As a result, hackers can get hold of SIP information by accessing the VoIP server or the existing phone system. With spoofing or hijacking a SIP call, hackers can do this although it would require a large target group.
3) Is VoIP more secure than a cell phone?
Ans: As long as you have a strong internal IT infrastructure, VoIP calls are as secure as traditional phone systems. External hackers can’t intercept thea data as long as the calls are being made within the internal system. But there are vulnerability issues if the calls are made outside.
Summary:
With the increasing popularity of VoIP, schemes that are superior to the system will become more powerful and complex. VoIP providers and companies must work together to ensure the full security of their networks. By analyzing traffic and protecting the network, they can detect signs of fraud. As a result, VoIP providers can minimize the risk of fraud. Sadly, VoIP fraud will continue to be a profitable criminal activity.




